I’ve built a new sample that leverages Keycloak to do authentication and authorization in Quarkus applications. This article describes how to set up Keycloak in OpenShift, for example Red Hat OpenShift on IBM Cloud.
Get the code from GitHub.
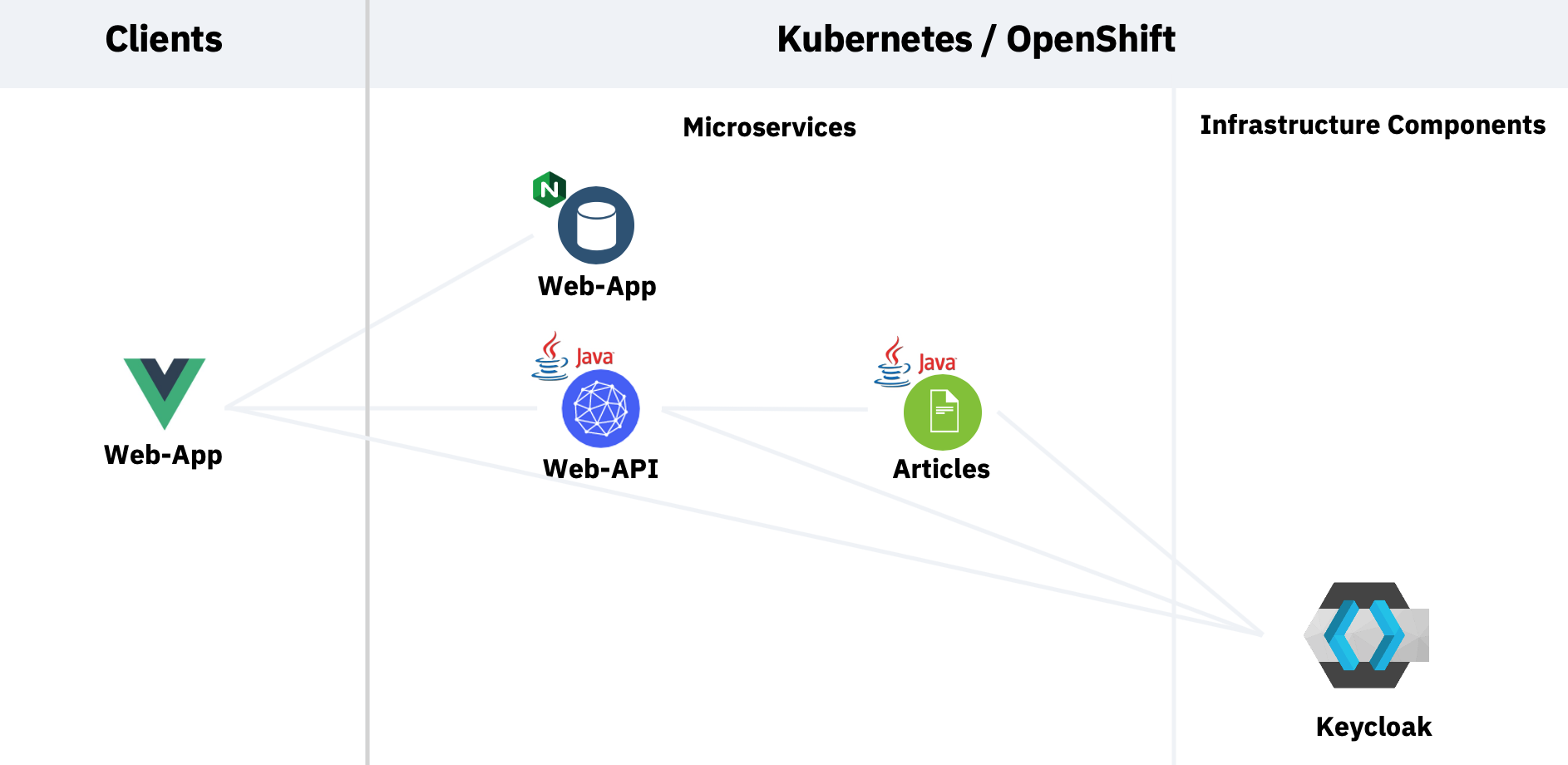
My sample contains a web application which invokes an API microservice and then one invokes a second microservice. To see the results in the web application users need to be authenticated and they need to have the role ‘user’. Here is the architecture.
The Keycloak documentation describes pretty well how to install Keycloak in OpenShift. The difficult part was the creation of the realm.
Quarkus comes with two great quides that describe how to use Keycloak in web apps and services which require different realm definitions. I’ve merged these two definitions so that they can be imported in one step.
- Using OpenID Connect to Protect Service Applications
- Using OpenID Connect to Protect Web Applications
The client frontend is used by the web application, the client backend-service for the two Quarkus microservices. Additionally a test user is created with the role ‘user’.
The documentation also contains commands that you can run the get the Keycloak URLs and the credentials of the admin, so that you can log in.
$ oc get secret credential-example-keycloak -o go-template='{{range $k,$v := .data}}{{printf "%s: " $k}}{{if not $v}}{{$v}}{{else}}{{$v | base64decode}}{{end}}{{"\n"}}{{end}}'
$ KEYCLOAK_URL=https://$(oc get route keycloak --template='{{ .spec.host }}')/auth &&
echo "" &&
echo "Keycloak: $KEYCLOAK_URL" &&
echo "Keycloak Admin Console: $KEYCLOAK_URL/admin" &&
echo "Keycloak Account Console: $KEYCLOAK_URL/realms/myrealm/account" In my next article I’ll explain how to do authentication and authorization in Quarkus applications.