The Bluemix Vulnerability Advisor checks the security status of container images before deployments as well as the status of running containers. For example it can detect weak passwords, whether SSH is installed or whether images have known vulnerabilities.
The Vulnerability Advisor leverages various sources like the CentOS announce archives and Red Hat RHSA announce archives to know about vulnerabilities and it calculates risk based on the IBM X-Force Exchange technology.
While this functionality has been available for scalable containers groups for quite some time, you can also use this functionality now in DevOps Delivery Pipelines when deploying Kubernetes applications. There is a nice tutorial that describes in detail how to set up a hello world sample. Below is a quick summary.
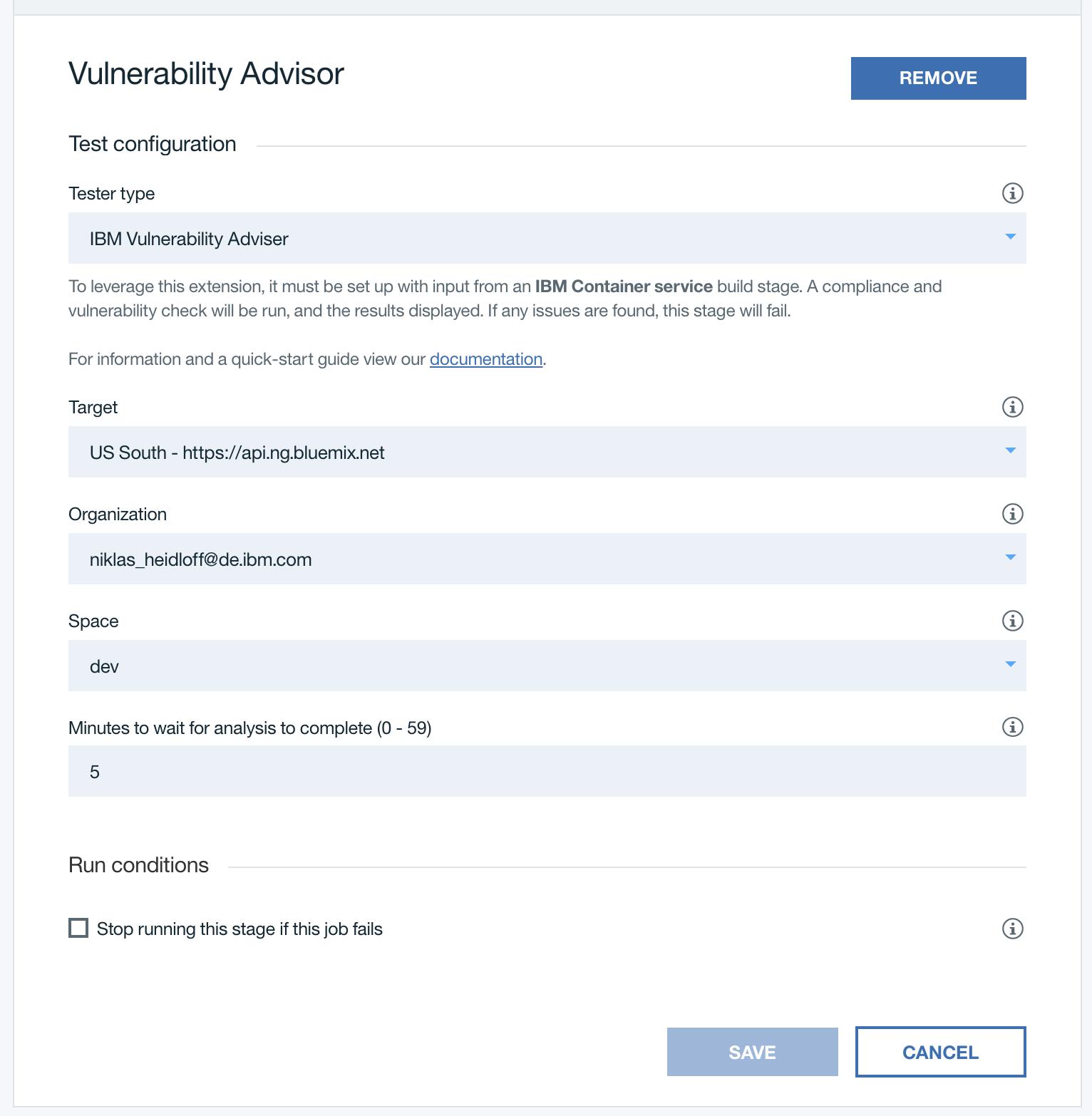
In Delivery Pipelines you can add stages with the tester type “IBM Vulnerability Advisor” which checks all images of a Kubernetes application. At the bottom of the screenshot is a checkbox to define whether you want to stop running the pipeline if this stage fails.
Since the currently latest version of the node image from Docker hub has vulnerabilities, the deployment of the sample application is prevented. To fix these issues the node image provided by IBM (registry.ng.bluemix.net/ibmnode) is used instead.
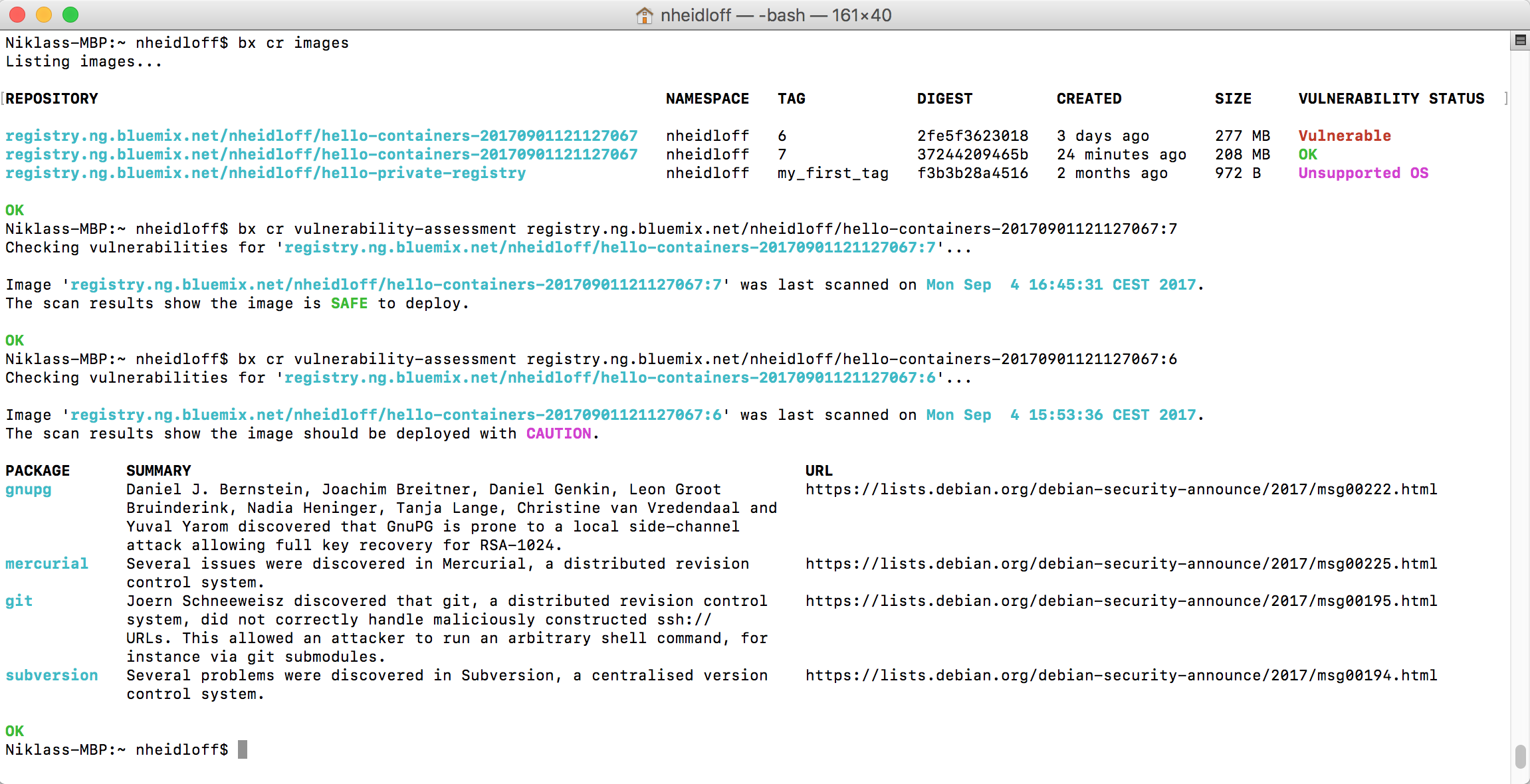
The screenshot shows how to read the output of the advisor via the ‘bx cr’ CLI. Alternatively you can also see this information in the Bluemix web user interface.
To lean more about the Vulnerability Advisor read the documentation.